How should a trading platform handle your API keys?6 min read
Table of Contents
A trading platform is a crucial tool for any trader, offering a range of features and services that can help you execute trades or manage your portfolio. One important aspect of a trading platform is how it handles your API keys, which are used to connect your trading platform to your exchange account. In this article, we will explore how a trading platform should handle your sensitive information, why it’s important to use a secure platform, and what you can do to ensure the safety of your keys.
Is it safer to install the trading software on your PC or have it run in the cloud?
Installing software on your PC at home and whitelisting the IP, is only as secure as your home network. Those, mind you, are being breached orders of magnitude more often than cloud servers networks. Not to mention the potential of downloading and installing malicious software right off the bat.
So, the real question is how many and how strong “barriers” are between your API Key/Secret and a potential party with bad intentions?
Running software in the cloud offers some security advantages over installing it on your home PC. Cloud servers are typically more secure than home networks, as they are subject to regular security audits and updates. Additionally, cloud-based software is generally easier to keep up-to-date and secure, as updates are managed by the cloud provider. However, it’s still important to choose a reputable cloud provider and to use best practices for securing your API keys, regardless of whether the software is running on your home PC or in the cloud.
How does cleo.finance store my API and Secret keys?
In cleo.finance, there is nothing we take more seriously than security and that’s why keep up with the best industry standards. Without going too much into detail, a few security barriers we use include:
- Main servers manipulating any sensitive data are not visible to the outside network at all
- Your API key/secret is not stored in a single database but is stored in 3 different places, each with separate hardware and software security protections
- The attacker would have to breach all 3 to get access to the Encrypted version of API key/secret – which wouldn’t help them all
- Those sensitive data are encrypted with arguably the most modern and secure 256-bit encryption protocol
- Brute-force decrypting of the data from a single database with current technology would take longer than the age of our universe.
- Our cloud hardware is distributed and the software is up-to-date with the most recent security updates
- We also use more security systems to protect our users’ data, such as employee-specific access limitation policies and much more, but we would like to keep those private
What can I do to increase the security of my funds if I want to use cleo.finance or any other third-party software?
There are many easy tasks you can perform to ensure everything on your end is as watertight as possible when you’re creating your API keys (Guides on how to generate API keys on exchanges are here: OKX and Binance).
1. Watch out for phishing schemes
To prevent and identify phishing scams, you should be cautious when clicking on links or opening attachments in emails, even if the email appears to be from a legitimate source. You should also be wary of providing personal information, such as passwords or credit card numbers, on unfamiliar websites. If a website or email appears suspicious, either do a quick online search to see if other users have reported it as a phishing scam. If you are unsure if you are on a phishing site, you should not enter any personal or sensitive information and should contact the organization the email claims to be from to verify the legitimacy of the website.
Reminder: Cleo.finance will never ask you to provide your API key, or any other security credentials, personal details, or similar, via email, chat, Facebook, Telegram, Twitter, or any other social network.
2. Whitelisting IP addresses can help to increase the security of your funds when using any third-party software.
By limiting access to your exchange account only to known IP addresses, you can prevent a significant amount of unauthorized access attempts. However, for trading platforms serving thousands of users, such as cleo.finance, exposing the IP addresses of trading servers is a security and scalability issue on its own. OKX exchange created a nice workaround, where the trading platform provides the list of IP addresses to whitelist to the exchange directly, thus limiting the circle of potential malicious actors.
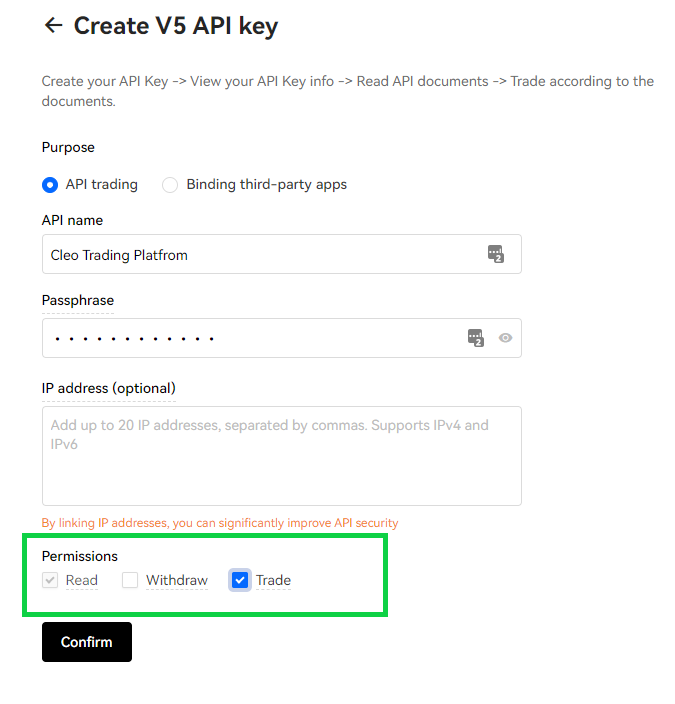
3. Allow only necessary access to your exchange account in the API key permission settings.
For example, you can grant read-only access to tax software or trading journal software. This allows the platform to view your account information but not execute trades or withdraw funds. Alternatively, you can grant read + trading access, which allows the platform to view your account information and execute trades but not withdraw funds. It’s important to never allow withdrawals, as this can leave your funds vulnerable to unauthorized access.
4. Limit the number of third-party services you use and use a different API key for each of them.
The more services you connect to your exchange account, the more potential vulnerabilities there are. By limiting the number of services you use, you can reduce the potential for unauthorized access to your account. Using different API keys for each of them can help figure out where the breach is coming from.
5. Regularly update your API keys.
By deleting old API keys and creating new ones, you can ensure that your exchange account remains secure. This is particularly important if you suspect that one of your API keys has been compromised. By regularly updating your keys, you can prevent unauthorized access to your account and keep your funds safe.
In conclusion, it’s important to choose a trading platform that handles your API keys securely. By following the best practices outlined in this article, you can increase the security of your funds and protect your exchange account from unauthorized access. By using separate API keys for each platform, limiting the number of third-party services you use, allowing only necessary access permissions, and regularly updating your API keys, you can ensure that your funds remain safe and secure while using a trading platform like cleo.finance.





